
Setting up TLS using Letsencrypt with cert-manager
Setting up a website with TLS makes a lot of sense, and with cert-manager / LetsEncrypt, you get free TLS certs that automatically renew. You then do not have to worry about people sniffing your credentials, and doing all kinds of other nefarious things.
Explaining how this tool works is a bit beyond the scope of what I want to do in this article, suffice it to say that we are setting up infrastructure to order, install, and renew TLS certificates for your domain automatically. You can find more information on this tool here.
Install with:
kubectl apply -f https://github.com/cert-manager/cert-manager/releases/download/v1.14.3/cert-manager.yaml
Once this is done, copy and edit this manifest, replacing your email
apiVersion: cert-manager.io/v1
kind: ClusterIssuer
metadata:
name: letsencrypt-prod
spec:
acme:
email:YOUR-EMAIL@YOU.COM
server: https://acme-v02.api.letsencrypt.org/directory
privateKeySecretRef:
name: letsencrypt-prod
solvers:
- http01:
ingress:
class: traefik
Note that this just sets up the infrastructure. To test,
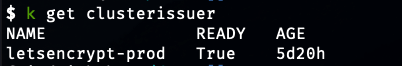
with k being an alias for kubectl. After a minute or so, this should be true. You can also check that the cert-manager pods are up
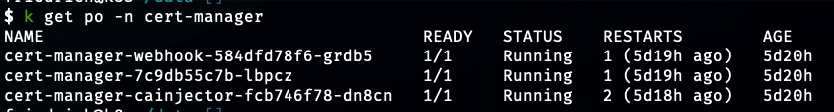
The above shows the pods in a healthy state. Adding an ingress to the cluster with magic annotations, will cause cert-manager to generate a tls secret for you. It will store this in a k8s secret, which you can use on your real ingress annotation to terminate TLS. More about how that works later, the setup step is now complete. The cert will only be good for a few months, but the cool thing is — cert-manager will renew it automatically before it expires.
Adding Traefik redirect middleware
Just so we don’t forget, we want to enable http -> https redirection. Note that the manifests below is just required infrastructure that will allow us to configure the redirect.
apiVersion: traefik.containo.us/v1alpha1
kind: Middleware
metadata:
namespace: default
name: redirect-https
spec:
redirectScheme:
scheme: https
permanent: true
Case you are wondering what traefik is — its a reverse-proxy built into k8d. It runs listening to ports 80 and 443, and redirects traffic to services if being told to do this by an ingress rule. I believe it is the responsible for terminating TLS as well.
